Ads

If the hands-off cooking methods and fall-apart tender meat doesn’t make corned beef an annual tradition at your house, we don’t know what will.
World's #1 Trusted Info Resource
108K
Original Posts
6.9M+
Ratings & Reviews
50M
Engaged Views
The Latest
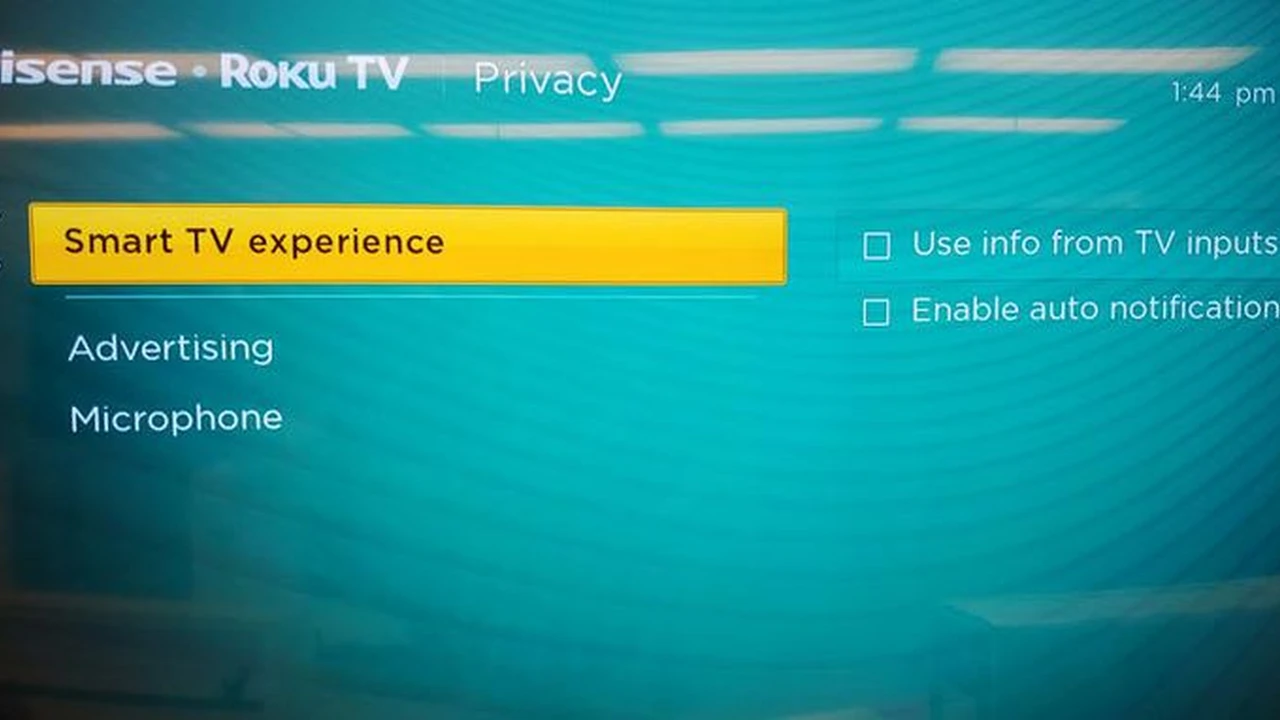
- Smart Devices and IoT Security
- |
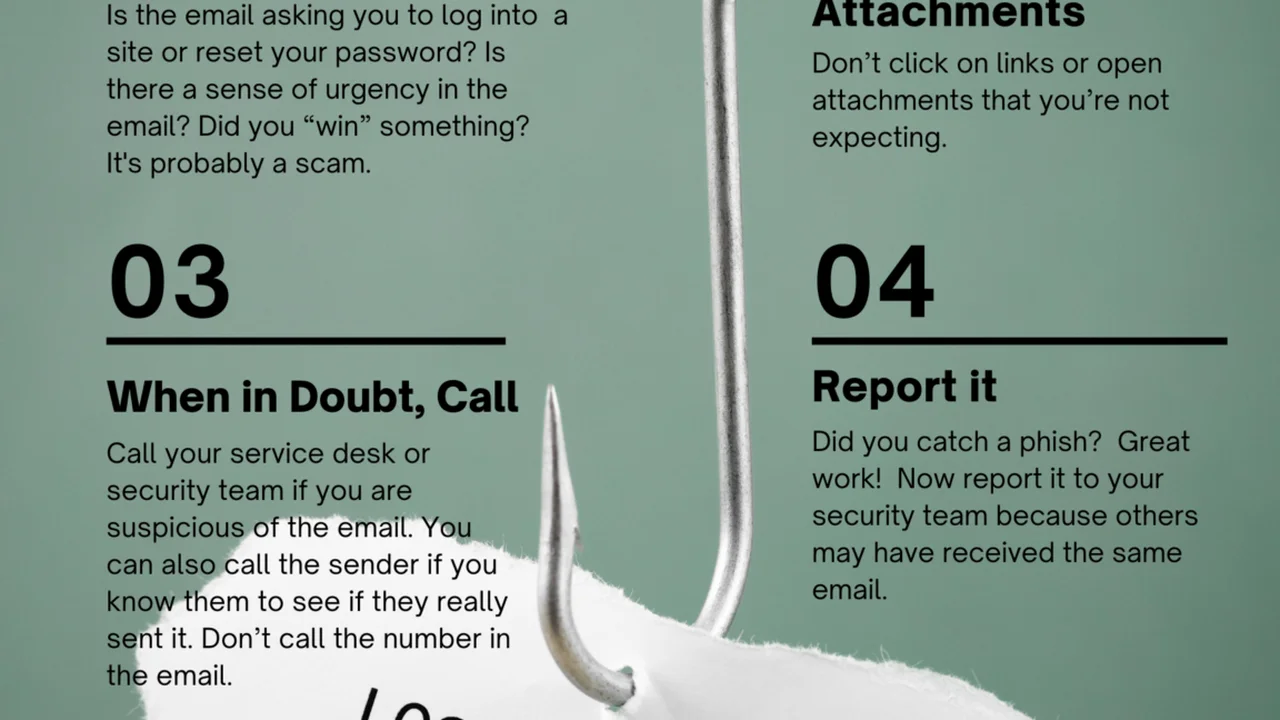
- Cybersecurity Best Practices and Tools
- |
- Cybersecurity Best Practices and Tools
- |
- Cybersecurity Best Practices and Tools
- |
- Smart Devices and IoT Security
- |
World's #1 Trusted Info Resource
- 108K Original Posts
- 6.9M+ Ratings & Reviews
- 50M Engaged Views

If the hands-off cooking methods and fall-apart tender meat doesn’t make corned beef an annual tradition at your house, we don’t know what will.
The Latest
- Smart Devices and IoT Security
- |
- Cybersecurity Best Practices and Tools
- |
- Cybersecurity Best Practices and Tools
- |
- Cybersecurity Best Practices and Tools
- |
- Smart Devices and IoT Security
- |

What would you like to know about?
Trending Now
- Smart Devices and IoT Security
- Cybersecurity Best Practices and Tools
- Cybersecurity Best Practices and Tools
- Cybersecurity Best Practices and Tools
Hot Articles
HOLIDAYS AND EVENTS RECIPES
- Smart Devices and IoT Security
- Cybersecurity Best Practices and Tools
- Cybersecurity Best Practices and Tools
- Cybersecurity Best Practices and Tools
- Smart Devices and IoT Security